Its activities in social media, electronics, and semiconductors should be particular causes for concern, as they are a means of infiltrating Western societies and economies in order to surreptitiously gather data for both economic and geopolitical advantage.
While China’s TikTok can apply the Google model of data-harvesting to its Western users and feed the data analysis to the China Communist Party (CCP), surveillance cameras with “China Inside” are watching our shopping malls, industrial facilities, offices, and increasingly “smart” cities.
Allies of the U.S. have recently been under pressure to implement a ban on Huawei telecommunications equipment. They should also think carefully about following the U.S. lead on surveillance cameras to stop the data being harvested from falling into the wrong hands.
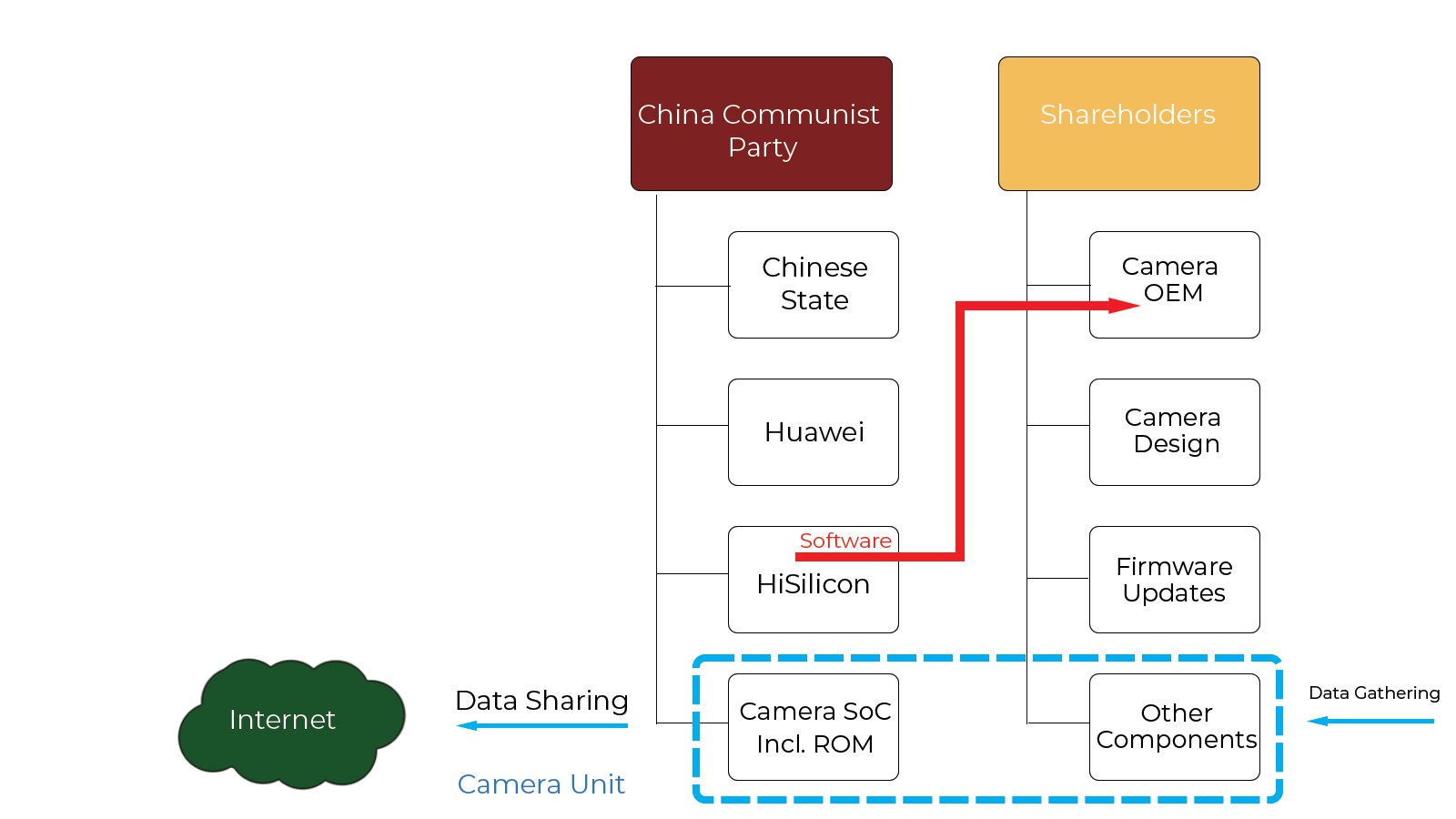
Fig.1 — Chain of Ownership & Control for a Camera Unit
The U.S. has sanctioned Dahua and Hikvision, two Chinese firms that are the world’s leading security camera suppliers, under the 2019 National Defense Authorization Act (NDAA). Western companies such as Honeywell and Swann are affected by models made in Chinese factories. Although the NDAA itself did not explain the reason for the ban, those who voted for it cited human rights abuses, lack of cybersecurity safeguards, and a belief that the banned cameras can be used for mass-espionage.
Most cameras currently shipped contain Chinese-designed and Chinese-made components, particularly the camera SoC (System-on-Chip) which acts as the control center. The market-leading provider of camera SoCs, with over 500 million units shipped, is China’s HiSilicon, the wholly owned silicon chip subsidiary of the state-owned technology giant Huawei (see fig.1). Cameras based on HiSilicon’s SoC have been covered by the NDAA ban since August 2020. However, to the best knowledge of the author, U.S. allies have not yet extended their bans on Huawei to include HiSilicon-powered cameras.
Why are such cameras banned by the NDAA? To understand this, it is useful to know that the SoC contains a processor, or CPU, which operates under software instructions, just like a computer. But unlike computers, devices such as cameras and smartphones do not contain a hard disk, so the software has to be stored in a memory that retains its data once power is switched off. It is thus usually known as “firmware”, and is stored in two types of this “non-volatile” memory:
- Flash memory, which can be electrically erased and reprogrammed: this stores the software updates that you download to your smartphone, and that the surveillance camera will download autonomously if so enabled. This firmware is under the control of the device OEM, which delivers it from a secure download site.
- Read-Only Memory, or ROM: this stores a program that is permanently burned into the camera SoC by the SoC vendor, and cannot be changed once the SoC has been fabricated. Its design and implementation is entirely under the control of the SoC vendor.
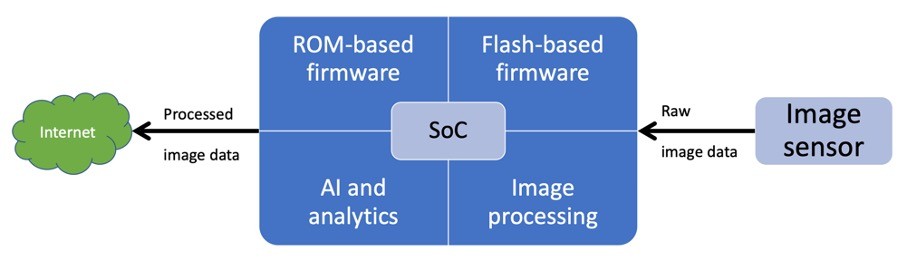
These two pieces of firmware work together for device function. The ROM in the SoC normally controls low-level functions such as boot-up, communication links to/from the SoC, and the download and installation of the Flash-based firmware. The Flash memory holds the main operating system (“OS”), which is regularly updated, as well as software applications which can run on the OS (known as “apps” on a smartphone).
When CCTV systems were first introduced, cameras were “dumb” units that just collected footage viewed on TV screens as it happened. Storage was on videotape, and later hard disk drives. Searching stored footage manually is a time-consuming process, so video management systems were developed which could not only store the image data, but analyze it automatically, saving valuable time. Thus motion detection, face detection/recognition, voice alerts, and a whole host of other applications known as analytics became common features in cameras.
Analytics were initially run on the video management systems, then on remote servers in the cloud. But as the market for “dumb” cameras became increasingly commoditized, it became commonplace to build some of these features into the camera itself, thus adding value for the camera OEM. However, all these analytics are either under the control of the camera SoC, or implemented inside it. As the SoC became more and more complex, those vendors able to make the biggest investments to add the most analytics, whilst maintaining price competitiveness, took the largest market share. This is what HiSilicon has successfully achieved: by 2015, 60% of all IP cameras shipped globally used a HiSilicon SoC. U.S. and European OEMs such as Honeywell were amongst its customers as well as the more obvious Hikvision and Dahua.
Another change was driven by the need for security for small business and domestic purposes, for which maintaining the closed circuit of CCTV was too costly and impractical. For this market, cameras connected to the internet using standard interfaces were required, and thus internet protocol (IP) cameras were developed. These are now the standard for all applications, with a dependence on internet firewalls as the safeguard against external access of data.
As a result of these developments, surveillance cameras have become increasingly sophisticated and autonomous, with the capability to make decisions as to what data to capture, how to process it, when to connect to the internet, and what is sent over it. Its behavior is determined by the firmware instructions in its ROM and Flash. As we have seen, the ROM contents are entirely under the control of the SoC provider, who also makes software releases to the camera OEM to incorporate into software updates. These may be made mandatory for camera maintenance.
So an SoC vendor, such as HiSilicon, is in the powerful position of being able to implant firmware code which controls the camera and is almost undetectable. This code could instruct the camera to capture images triggered by certain events, and send analyzed data over the internet to a third party outside of the OEM/installer/end user relationship.
Fig.2 — Camera Components and Functions
Is it possible to find out whether the SoC vendor is attempting to use the camera as a trojan horse in this way? Yes, by one of two means:
- Source code disclosure — the manufacturers of the camera and its SoC make the firmware available in its original human-readable form. The end-user or installer can then try to reconstruct the camera behavior, bottom up.
- Test and audit procedures — the camera is subjected to a number of test conditions and its performance is logged and analyzed, top-down.
In the case of (1), camera vendor Hikvision has indeed made its source code available for analysis. But HiSilicon has not done so for its camera SoC firmware, to the best knowledge of the author. Even if it had, validating that the disclosed code exactly matches that programmed into the ROM is very difficult and costly, requiring a time-consuming process known as disassembly. For (2), it is not possible to produce an exhaustive set of test cases, which will inevitably try to simulate expected real-world behavior. Unexpected behaviors, such as sending the location of particular person if they are recognized by the camera, cannot all be tested for.
So why does this matter?
- The intelligence behind the data collection, data processing, and data sharing performed by surveillance cameras is embedded in the silicon chip that controls the camera known as the camera SoC.
- The Chinese vendor Hisilicon has a dominant market share of these silicon chips for surveillance cameras that connect to the internet, known as IP cameras.
- The firmware that is hard-wired into silicon chips by means of their ROM is the product of Hisilicon, a subsidiary of Huawei, itself an arm of the Chinese state.
- Implantation of firmware code into ROM that performs surreptitious surveillance would be extremely difficult and costly to detect by the installer or end-user.
- Allies of the US who do not follow the lead of the 2019 NDAA are therefore leaving the door open to Chinese state-sponsored data harvesting and hence China Communist Party influence over their economies and people.